Stormy Seas Ahead: Top 5 Malware Threats in 2012
 If you know me, you know I’m not really prone to spreading security FUD. I’ve been asked to prognosticate a bit about the near-term future, and I have to say, without intending to sound like a fearmonger, the next year is shaping up to be pretty messy from a security perspective. I have a hard time finding any silver linings to the massive storm clouds that seem to hang all around and on top of us.
If you know me, you know I’m not really prone to spreading security FUD. I’ve been asked to prognosticate a bit about the near-term future, and I have to say, without intending to sound like a fearmonger, the next year is shaping up to be pretty messy from a security perspective. I have a hard time finding any silver linings to the massive storm clouds that seem to hang all around and on top of us.
Right now, the climate for attacks is just brutal. Based on what I’ve been seeing since Halloween, if the pace and volume of attacks keep up, the coming year doesn’t look like it’s going to be pretty. Rampant spam-driven attacks, multiple manifestations of classic social engineering scams, corporate espionage, and malware malware malware look to be on the table for 2012. It was hard to winnow my worst-of-the-worst list down to only five items, but I had to draw the line somewhere, and it seems like a nice, round number.
So, with that in mind, click through the jump to read my top five threats to watch for in 2012.
Increasing use of compromised, legitimate sites from which to stage attacks
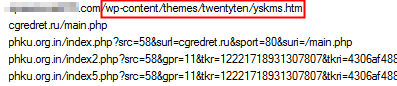
It doesn’t matter whether you own a tiny art collective or you operate an organization as large as Amnesty International: The continued existence of unpatched, vulnerable Web site code — in particular, vulnerable WordPress.org blog plugins — are set to become a big problem in the near future; that, and a massive flood of keylogger malware washing across the net means we’ll see a lot of sites get pwned in the coming year and used, like the one in the screenshot above, to redirect victims into an exploit kit.
The WordPress.org plugin vulnerabilities permit malware guys to upload their code onto someone else’s Web pages; Keylogger malware, such as Zeus/Zbot, just rips saved FTP passwords and other stored credentials and ships them directly to People You Don’t Want In Control Of Your Web Site.
It’s already happening, with “TimThumb“-style attacks propagating against other vulnerable WordPress.org code, and the results have been pretty scarily effective. Most of the code we’ve seen uploaded to legit sites redirects the browser into the maw of one or another exploit kits.
Scripted exploits targeting vulnerable browser plug-ins
If you’re not running Firefox with NoScript installed, you need to do so right now. As far as I can tell, it’s the only surefire method of preventing an accidental infection of a Windows PC by exploit-kitted Web pages. It all starts with a blob of heavily-obfuscated Javascript and ends within a few minutes with the victim’s PC pwned and the victim’s passwords in the hands of some Asian or eastern European goon squad.
It couldn’t get any more obvious that you need to act immediately. Update Flash, Acrobat, Office, and other vulnerable applications today, right now. Disable Javascript within PDF documents in your PDF reader’s preferences. And at least for the time being, the safest thing to do is to uninstall Java from any system you control, at least until a patch gets released to address CVE-2011-3544.
Give us a break with the spam, already
As patently ridiculous as some of the spam campaigns this year have been, they must be effective, because the bad guys haven’t spared a moment for months coming up with new and innovative social engineering tricks.
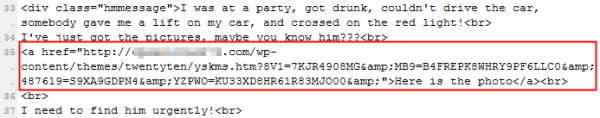
If the spam we’ve seen is any indication, malicious spam we receive in 2012 will come in every available delivery method — email, social networks, IM — and continue to take every conceivable form: shipping confirmations, missed deliveries, reversed credit warnings, utility bills, credit card statements, complaints about you to the Better Business Bureau (whether or not you operate a business), online order confirmations from small boutique etailers, bank statements, electronic funds transfer rejection notices, poorly-spelled ‘friend notification’ emails from a wide variety of social networking sites. And yes, even I got drunk, had a stranger drive me home, but then the stranger got a ticket for running a red light, and now I need to find him contrivances. Seriously, who comes up with this crap?
The list just never seems to end. It’s getting ridiculous. The big question remains which infection method will take the crown: zipped malware attached to the messages, or links to malicious pages and driveby downloads. Right now the two distribution techniques are running neck-and-neck.
Is that your SCADA system hanging out there for everyone to see?
When people mention SCADA systems and security risks, many first think of attacks against secretive nuclear facilities in a hot desert. But SCADA systems don’t just control plutonium enrichment centrifuges. They control things as mundane as the hot water boilers in large steam heating systems, the electrical systems of large office buildings, and the telephone switches in hospitals and universities. They’re everywhere, all around us, and there are just a huge number of them wide open to the world, where people can simply poke at them until they break open the crown jewels.
‘Messing around’ is already happening, and the false alarm over the Springfield, IL water treatment plant should have served as a wake-up call. Even though the water system’s network had never been penetrated by outsiders, the idea of such a thing happening is well within the realm of possibility and edging ever closer to “actually happened” every day. If the operators of these systems, worldwide, don’t take immediate action to lock down the public Web interface to their SCADA-controlled devices, it could be only a matter of time before some sociopath decides to cause deliberate harm, shutting off a critical system in a time of need.
Smartphones, personal data, and malicious apps (oh my!)
I don’t want to leave my friends in the mobile world out of the fun list. The sheer volume of copycat Android malware coming out of, in particular, China is just astonishing. There are whole Markets hosted overseas just rippling with malicious badness, as well as ripoff artists on this side of the pond trying to scam whatever they can.
Here’s my Cool Story, Bro Android malware story for 2011: This year, I bought a cheapo knockoff Android tablet for research purposes; I won’t name the seller or manufacturer at this time. The tablet didn’t come with the Google Market installed. Instead it came with a link to some alternative market I’d never heard of. Literally every single app I downloaded (and I spent a few whole days just grabbing one file after another) asked for every conceivable permission upon installation. Every. One. Seven screens worth of descriptive text. The photo above a small number of those permission requests.
I don’t see this slowing down anytime soon, so take great care with anything you install to your smartphone (or even your cheapo tablet), especially if you’ve rooted or jailbroken it.














Trackbacks
Comments are closed.